Suricata vs Zenarmor
August 05, 2023 | Author: Michael Stromann
See also:
Top 10 Firewall software
Top 10 Firewall software
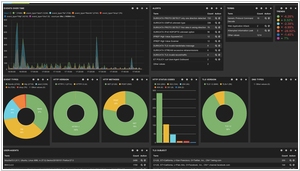
Suricata and Zenarmor are two distinct network security solutions, each with its own set of features and use cases. Suricata is an open-source intrusion detection and prevention system (IDS/IPS) that provides real-time network traffic analysis and threat detection capabilities. It uses signature-based rules and advanced behavior analysis to identify and block malicious traffic, making it effective in defending against a wide range of cyber threats. Suricata is a versatile tool suitable for organizations seeking a cost-effective, customizable solution with active community support and continuous development.
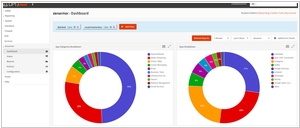
On the other hand, Zenarmor is a commercial network security platform that focuses on application-layer security. It offers advanced web application firewall (WAF) capabilities to protect web applications from various attacks, including SQL injection, cross-site scripting (XSS), and DDoS attacks. Zenarmor's strength lies in its specialized protection for web applications and its ability to provide deep visibility into HTTP/HTTPS traffic, enabling organizations to proactively secure their web assets. It is particularly beneficial for companies with web-based services that require robust protection against web-based threats.
One significant difference between Suricata and Zenarmor is their primary use cases. Suricata is an IDS/IPS solution that offers broader network security capabilities, including the detection of network-based threats beyond web applications. In contrast, Zenarmor is focused on providing advanced security for web applications specifically. Organizations should evaluate their security needs and consider factors such as the types of threats they want to protect against, the level of customization required, and the specific assets they need to secure (e.g., general network traffic or web applications) to determine which solution aligns best with their requirements.
See also: Top 10 Firewall software
On the other hand, Zenarmor is a commercial network security platform that focuses on application-layer security. It offers advanced web application firewall (WAF) capabilities to protect web applications from various attacks, including SQL injection, cross-site scripting (XSS), and DDoS attacks. Zenarmor's strength lies in its specialized protection for web applications and its ability to provide deep visibility into HTTP/HTTPS traffic, enabling organizations to proactively secure their web assets. It is particularly beneficial for companies with web-based services that require robust protection against web-based threats.
One significant difference between Suricata and Zenarmor is their primary use cases. Suricata is an IDS/IPS solution that offers broader network security capabilities, including the detection of network-based threats beyond web applications. In contrast, Zenarmor is focused on providing advanced security for web applications specifically. Organizations should evaluate their security needs and consider factors such as the types of threats they want to protect against, the level of customization required, and the specific assets they need to secure (e.g., general network traffic or web applications) to determine which solution aligns best with their requirements.
See also: Top 10 Firewall software