Snort vs Tripwire
August 06, 2023 | Author: Michael Stromann
See also:
Top 10 Intrusion Detection Systems
Top 10 Intrusion Detection Systems
Snort and Tripwire are two widely used cybersecurity tools that serve different purposes and address distinct aspects of cybersecurity.
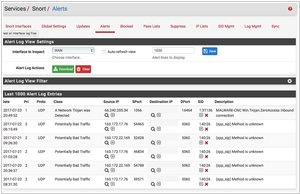
Snort is an open-source intrusion detection and prevention system (IDS/IPS) that focuses on real-time network traffic analysis. It is designed to monitor network packets and identify suspicious or malicious activity. Snort uses signature-based detection and can be configured to detect a wide range of threats, including viruses, worms, and network-based attacks. The system can alert security administrators in real-time, allowing them to respond swiftly to potential threats. Snort's strength lies in its ability to analyze network traffic and identify threats before they can cause significant damage, making it a valuable addition to any organization's cybersecurity arsenal.
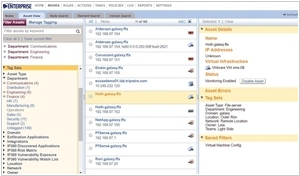
Tripwire, on the other hand, is a file integrity monitoring (FIM) tool that emphasizes system integrity and compliance. It works by monitoring critical files and directories, detecting any unauthorized changes to them. Tripwire uses cryptographic hash functions to create a baseline of known, trusted files, and then compares subsequent changes against this baseline. If any unauthorized modifications are detected, Tripwire can alert administrators and potentially halt suspicious activity. This focus on integrity monitoring ensures that system configurations and files remain unchanged and secure, which is crucial for compliance and maintaining a secure IT environment.
See also: Top 10 Intrusion Detection Systems
Snort is an open-source intrusion detection and prevention system (IDS/IPS) that focuses on real-time network traffic analysis. It is designed to monitor network packets and identify suspicious or malicious activity. Snort uses signature-based detection and can be configured to detect a wide range of threats, including viruses, worms, and network-based attacks. The system can alert security administrators in real-time, allowing them to respond swiftly to potential threats. Snort's strength lies in its ability to analyze network traffic and identify threats before they can cause significant damage, making it a valuable addition to any organization's cybersecurity arsenal.
Tripwire, on the other hand, is a file integrity monitoring (FIM) tool that emphasizes system integrity and compliance. It works by monitoring critical files and directories, detecting any unauthorized changes to them. Tripwire uses cryptographic hash functions to create a baseline of known, trusted files, and then compares subsequent changes against this baseline. If any unauthorized modifications are detected, Tripwire can alert administrators and potentially halt suspicious activity. This focus on integrity monitoring ensures that system configurations and files remain unchanged and secure, which is crucial for compliance and maintaining a secure IT environment.
See also: Top 10 Intrusion Detection Systems