Shinobi vs motionEye
September 08, 2023 | Author: Michael Stromann
See also:
Top 10 Video Surveillance services
Top 10 Video Surveillance services
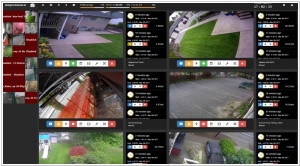
Shinobi and motionEye are two popular open-source video surveillance software solutions, each with its own set of features and capabilities. One key difference between the two lies in their primary focus and use cases. Shinobi is designed as a more comprehensive and extensible platform for video surveillance, offering advanced features like object detection, custom alerts, and support for a wide range of camera models. It provides a robust framework for building a complete surveillance system, making it suitable for both home and professional use.
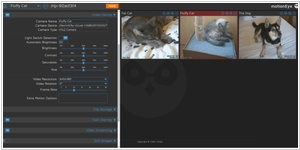
On the other hand, motionEye takes a simpler and more user-friendly approach. It is primarily focused on providing a lightweight and easy-to-use interface for setting up and managing IP cameras. While motionEye lacks some of the advanced features found in Shinobi, it excels in simplicity and is a great choice for users looking for a quick and straightforward way to set up basic surveillance with minimal configuration. This makes motionEye ideal for beginners or those with simpler monitoring needs.
Another significant difference is the level of customization and control offered by each platform. Shinobi allows users to fine-tune their surveillance system to meet specific requirements, making it a more versatile option. It offers features like scripting support and extensive configuration options, giving advanced users the ability to tailor the system to their needs. In contrast, motionEye is more limited in terms of customization, offering a straightforward setup process that may not suit users seeking extensive control over their surveillance system.
See also: Top 10 Surveillance Systems
On the other hand, motionEye takes a simpler and more user-friendly approach. It is primarily focused on providing a lightweight and easy-to-use interface for setting up and managing IP cameras. While motionEye lacks some of the advanced features found in Shinobi, it excels in simplicity and is a great choice for users looking for a quick and straightforward way to set up basic surveillance with minimal configuration. This makes motionEye ideal for beginners or those with simpler monitoring needs.
Another significant difference is the level of customization and control offered by each platform. Shinobi allows users to fine-tune their surveillance system to meet specific requirements, making it a more versatile option. It offers features like scripting support and extensive configuration options, giving advanced users the ability to tailor the system to their needs. In contrast, motionEye is more limited in terms of customization, offering a straightforward setup process that may not suit users seeking extensive control over their surveillance system.
See also: Top 10 Surveillance Systems