Keycloak vs Ping Identity
August 07, 2023 | Author: Michael Stromann
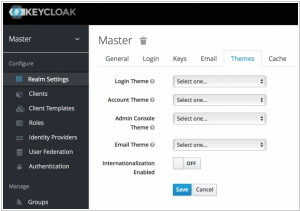
Keycloak and Ping Identity are both popular identity and access management (IAM) solutions, but they differ in their target markets and deployment options. Keycloak, developed by Red Hat, is an open-source IAM solution that offers robust features for managing user identities, authentication, and authorization in web applications and services. It provides developers with a flexible and customizable platform and supports Single Sign-On (SSO) capabilities. On the other hand, Ping Identity is a comprehensive IAM platform designed for enterprises, providing advanced security features, user lifecycle management, multi-factor authentication (MFA), and extensive integration capabilities. While Keycloak is well-suited for smaller organizations and development projects due to its open-source nature, Ping Identity is the go-to choice for large enterprises seeking a scalable, highly secure, and feature-rich IAM solution with extensive support and integration options.
See also: Top 10 Identity Management platforms
See also: Top 10 Identity Management platforms
Keycloak vs Ping Identity in our news:
2015. Ping Identity adds authentication via Apple Watch

Identity management platform Ping Identity has introduced a new feature that allows users to obtain their second authentication factor using an Apple Watch. The platform's concept revolves around prioritizing identity within the security framework, empowering users, including employees, partners, and customers, to access applications seamlessly across various devices, based on their unique identities. With Ping Identity, after signing in, your Apple Watch will vibrate, prompting you to activate it and tap the sign-on card displayed on the Watch. This innovative utilization of the Apple Watch offers a convenient and effective approach to streamline security measures.
2014. Identity management service Ping Identity lands $35M

Cloud security startup Ping Identity has secured a $35 million investment, highlighting the company's focus on mobile integration within its identity management platform. By leveraging a user's smartphone, Ping Identity ensures that the appropriate individuals gain access to specific parts of the network, thereby enhancing security measures. The identity and access management sector has witnessed notable activity this summer, with Okta securing a $75 million investment in June, and Sailpoint receiving an undisclosed investment valued at several hundred million dollars. These startups operate under the shared belief that the cloud has introduced complexities for companies to monitor access to their intricate internal networks, while simultaneously safeguarding against potential threats and unauthorized access.