Graylog vs Wazuh
August 06, 2023 | Author: Michael Stromann
See also:
Top 10 SIEM software
Top 10 SIEM software
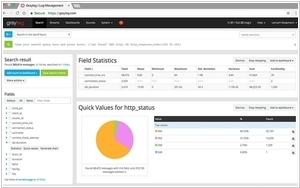
Graylog and Wazuh are both powerful log management and analysis solutions, but they have distinct focuses and features. Graylog is a comprehensive log management platform that excels in centralized log collection, storage, and analysis. It provides a user-friendly web interface for exploring and searching log data, along with features like alerting, dashboards, and user access controls. Graylog is designed to handle large volumes of log data efficiently and allows easy integration with various data sources, making it suitable for organizations seeking a comprehensive log management solution.
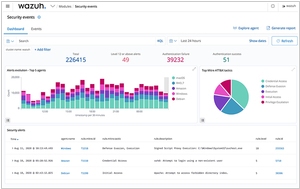
On the other hand, Wazuh is an open-source security monitoring platform that primarily focuses on host-based intrusion detection and log analysis. It leverages the OSSEC framework to provide real-time analysis of security alerts generated by log data and system events. Wazuh is highly versatile and extensible, allowing organizations to customize and integrate it with other security tools, offering greater flexibility in building a security stack tailored to their specific needs. Its focus on security monitoring makes it particularly suitable for organizations seeking to enhance their host-based security.
Another key difference lies in their primary use cases. Graylog is more centered around log management, providing centralized log collection, storage, and analysis capabilities, making it a valuable tool for IT operations and DevOps teams to gain insights from log data. Wazuh, on the other hand, is primarily designed for security monitoring and threat detection, with a focus on host-based intrusion detection and security log analysis, making it a preferred option for security operations and incident response teams seeking to enhance their security posture.
See also: Top 10 SIEM software
On the other hand, Wazuh is an open-source security monitoring platform that primarily focuses on host-based intrusion detection and log analysis. It leverages the OSSEC framework to provide real-time analysis of security alerts generated by log data and system events. Wazuh is highly versatile and extensible, allowing organizations to customize and integrate it with other security tools, offering greater flexibility in building a security stack tailored to their specific needs. Its focus on security monitoring makes it particularly suitable for organizations seeking to enhance their host-based security.
Another key difference lies in their primary use cases. Graylog is more centered around log management, providing centralized log collection, storage, and analysis capabilities, making it a valuable tool for IT operations and DevOps teams to gain insights from log data. Wazuh, on the other hand, is primarily designed for security monitoring and threat detection, with a focus on host-based intrusion detection and security log analysis, making it a preferred option for security operations and incident response teams seeking to enhance their security posture.
See also: Top 10 SIEM software