ElasticSearch vs Security Onion
August 06, 2023 | Author: Michael Stromann
See also:
Top 10 Big Data platforms
Top 10 Big Data platforms
Elasticsearch and Security Onion are two distinct solutions used in the domain of log management and cybersecurity, each with its specific focus and functionalities.
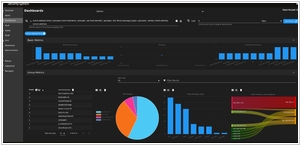
Elasticsearch, as discussed earlier, is an open-source distributed search and analytics engine known for its fast indexing and querying capabilities. It excels at aggregating and analyzing large volumes of data, making it suitable for log management, application monitoring, and full-text search. Elasticsearch is often used in conjunction with other components of the Elastic Stack, like Kibana and Logstash, to create a comprehensive data analytics platform. While Elasticsearch provides powerful data storage and retrieval, it does not include built-in security features, and organizations often need to integrate additional tools for access control and data protection.
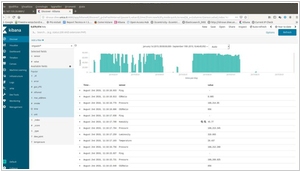
Security Onion, on the other hand, is a specialized open-source cybersecurity platform that focuses on intrusion detection, network monitoring, and incident response. It incorporates various security tools, including Intrusion Detection Systems (IDS), Network Security Monitoring (NSM), and log management systems, to provide comprehensive threat detection and analysis. Security Onion is designed to be deployed as a network security monitoring and intrusion detection system, allowing security teams to monitor network traffic and detect potential threats in real-time. It uses Elasticsearch as one of its components for log storage and indexing, but it also includes other essential tools and components tailored to cybersecurity use cases.
See also: Top 10 Big Data platforms
Elasticsearch, as discussed earlier, is an open-source distributed search and analytics engine known for its fast indexing and querying capabilities. It excels at aggregating and analyzing large volumes of data, making it suitable for log management, application monitoring, and full-text search. Elasticsearch is often used in conjunction with other components of the Elastic Stack, like Kibana and Logstash, to create a comprehensive data analytics platform. While Elasticsearch provides powerful data storage and retrieval, it does not include built-in security features, and organizations often need to integrate additional tools for access control and data protection.
Security Onion, on the other hand, is a specialized open-source cybersecurity platform that focuses on intrusion detection, network monitoring, and incident response. It incorporates various security tools, including Intrusion Detection Systems (IDS), Network Security Monitoring (NSM), and log management systems, to provide comprehensive threat detection and analysis. Security Onion is designed to be deployed as a network security monitoring and intrusion detection system, allowing security teams to monitor network traffic and detect potential threats in real-time. It uses Elasticsearch as one of its components for log storage and indexing, but it also includes other essential tools and components tailored to cybersecurity use cases.
See also: Top 10 Big Data platforms