Darktrace vs Vectra AI
August 05, 2023 | Author: Michael Stromann
See also:
Top 10 SIEM software
Top 10 SIEM software
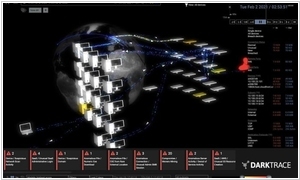
Darktrace and Vectra AI are both leading cybersecurity companies that specialize in AI-driven threat detection, but they employ different approaches and technologies to tackle the evolving cyber threats. Darktrace's flagship product is its Enterprise Immune System, which leverages unsupervised machine learning and AI algorithms to create a self-learning model of an organization's network. It focuses on anomaly detection, identifying unusual behavior within the network that may indicate potential threats. Darktrace's technology is designed to adapt and evolve alongside the network, providing real-time threat detection and response.
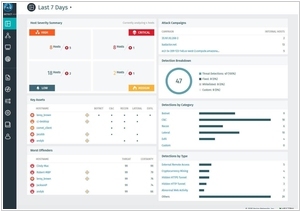
Vectra AI, on the other hand, specializes in network detection and response. Their platform is built on supervised machine learning, using behavioral analytics to monitor network traffic and identify threats, including insider threats and advanced cyberattacks. Vectra AI emphasizes its ability to provide high-fidelity alerts, reducing false positives and allowing security teams to focus on genuine threats efficiently. The platform also offers automated threat hunting and incident investigation features, streamlining the incident response process.
Another important distinction lies in the scope of their solutions. Darktrace's Enterprise Immune System and AI algorithms are not limited to network security but extend to cloud environments, IoT devices, and other digital infrastructure. This versatility enables Darktrace to provide a holistic view of an organization's security posture. Vectra AI, on the other hand, focuses primarily on network security, making it a valuable solution for organizations seeking specialized network threat detection and response capabilities.
See also: Top 10 SIEM software
Vectra AI, on the other hand, specializes in network detection and response. Their platform is built on supervised machine learning, using behavioral analytics to monitor network traffic and identify threats, including insider threats and advanced cyberattacks. Vectra AI emphasizes its ability to provide high-fidelity alerts, reducing false positives and allowing security teams to focus on genuine threats efficiently. The platform also offers automated threat hunting and incident investigation features, streamlining the incident response process.
Another important distinction lies in the scope of their solutions. Darktrace's Enterprise Immune System and AI algorithms are not limited to network security but extend to cloud environments, IoT devices, and other digital infrastructure. This versatility enables Darktrace to provide a holistic view of an organization's security posture. Vectra AI, on the other hand, focuses primarily on network security, making it a valuable solution for organizations seeking specialized network threat detection and response capabilities.
See also: Top 10 SIEM software