Corelight vs ExtraHop
August 06, 2023 | Author: Michael Stromann
See also:
Top 10 Intrusion Detection Systems
Top 10 Intrusion Detection Systems
Corelight and ExtraHop are both network security and monitoring solutions, but they have distinct approaches and features that set them apart.
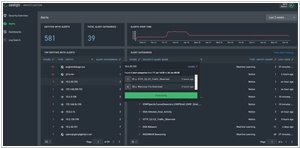
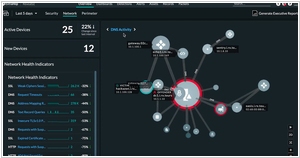
Firstly, Corelight is primarily based on the open-source network analysis framework Zeek (formerly known as Bro) and is designed to provide deep visibility into network traffic and security events. It excels in network forensics and threat hunting, offering detailed protocol analysis and metadata extraction to detect and investigate potential security incidents. Corelight is commonly used in large enterprises and security operations centers where advanced network traffic analysis is essential. On the other hand, ExtraHop takes a different approach by focusing on real-time analytics and machine learning. It leverages wire data, which means it captures and analyzes network packets in real-time to deliver actionable insights into application performance, user behavior, and security threats. ExtraHop is known for its ability to provide real-time visibility across complex, dynamic environments and is often used for performance monitoring, application troubleshooting, and anomaly detection.
Secondly, there is a difference in their deployment models. Corelight is typically deployed as a hardware appliance or a software sensor on the network, capturing and analyzing traffic at strategic points to provide deep insights. It is commonly integrated into existing security infrastructure and used in conjunction with other security tools. On the other hand, ExtraHop is offered as a software appliance or a virtual appliance that can be deployed on-premises or in the cloud. This flexibility makes ExtraHop a popular choice for cloud-native environments and organizations seeking more agile and scalable deployment options.
See also: Top 10 Intrusion Detection Systems
Firstly, Corelight is primarily based on the open-source network analysis framework Zeek (formerly known as Bro) and is designed to provide deep visibility into network traffic and security events. It excels in network forensics and threat hunting, offering detailed protocol analysis and metadata extraction to detect and investigate potential security incidents. Corelight is commonly used in large enterprises and security operations centers where advanced network traffic analysis is essential. On the other hand, ExtraHop takes a different approach by focusing on real-time analytics and machine learning. It leverages wire data, which means it captures and analyzes network packets in real-time to deliver actionable insights into application performance, user behavior, and security threats. ExtraHop is known for its ability to provide real-time visibility across complex, dynamic environments and is often used for performance monitoring, application troubleshooting, and anomaly detection.
Secondly, there is a difference in their deployment models. Corelight is typically deployed as a hardware appliance or a software sensor on the network, capturing and analyzing traffic at strategic points to provide deep insights. It is commonly integrated into existing security infrastructure and used in conjunction with other security tools. On the other hand, ExtraHop is offered as a software appliance or a virtual appliance that can be deployed on-premises or in the cloud. This flexibility makes ExtraHop a popular choice for cloud-native environments and organizations seeking more agile and scalable deployment options.
See also: Top 10 Intrusion Detection Systems