Cisco Umbrella vs iboss
August 05, 2023 | Author: Michael Stromann
Cisco Umbrella and iboss are two leading cybersecurity solutions, each offering unique strengths in protecting organizations from different aspects of digital threats. Cisco Umbrella, formerly known as OpenDNS, is a cloud-based security platform that focuses on DNS and web filtering. It provides extensive protection against malware, phishing, and other web-based threats by blocking malicious domains and analyzing internet traffic to identify potential risks. Its DNS-layer security ensures that devices are protected even when off-network. On the other hand, iboss specializes in cloud-based web security and offers advanced features like web filtering, malware defense, and data loss prevention. It empowers organizations to secure web traffic and cloud applications with granular control and robust threat protection. While Cisco Umbrella is renowned for its DNS-layer security and web filtering capabilities, iboss excels in providing comprehensive web-centric security solutions.
See also: Top 10 Cloud Security Software
See also: Top 10 Cloud Security Software
Cisco Umbrella vs iboss in our news:
2016. Cisco acquired cybersecurity-as-a-Service provider CloudLock
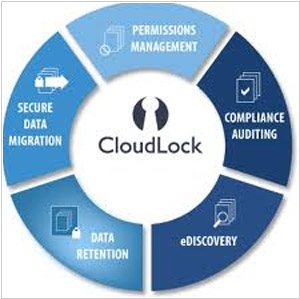
Cisco has revealed its intention to acquire CloudLock, a cloud-based security provider, for $293 million. CloudLock employs APIs to empower enterprises to apply and oversee security measures on shared and stored documents and other content within cloud-based applications. Its compatibility extends to popular applications like Office365, Google Drive, Salesforce, and numerous others. The primary focus of CloudLock lies in delivering robust security and enforcing policies to safeguard documents, regardless of the device used for accessing them. It also enables granular controls based on location, enhancing data protection capabilities.