Cisco Umbrella vs Microsoft Defender for Cloud
August 05, 2023 | Author: Michael Stromann
Cisco Umbrella and Microsoft Defender for Cloud are two leading cloud security solutions that offer distinct features to protect organizations from online threats. Cisco Umbrella, a cloud-based secure internet gateway (SIG) and DNS filtering solution, focuses on preventing access to malicious websites, URLs, and IPs. It acts as a first line of defense, filtering internet traffic and providing security at the DNS layer. On the other hand, Microsoft Defender for Cloud, formerly known as Microsoft Cloud App Security, is a comprehensive cloud security platform designed to protect cloud applications and services. It offers advanced threat protection, data loss prevention, and real-time visibility into cloud activities, helping organizations detect and respond to cloud-based threats effectively.
See also: Top 10 Cloud Security Software
See also: Top 10 Cloud Security Software
Cisco Umbrella vs Microsoft Defender for Cloud in our news:
2023. Microsoft 365 Defender is becoming Microsoft Defender XDR
Microsoft has integrated cloud workload alerts, signals, and asset information from Microsoft Defender Cloud into Microsoft 365 Defender - it's cloud-based service designed to help protect on-premise, cloud and hybrid environments. This integration now removes any infrastructure blind spots in an organization’s digital landscape. As part of this integration, the company is rolling out new correlations and content tailored to cross-workload correlations and cloud-specific content, giving you a richer, more contextual understanding of the threats, your organization faces. In the Defender portal, SOC analysts can now run end-to-end investigations if they’re faced with this type of cyberattack. They can monitor, triage, and investigate multicloud alerts across Azure, AWS, and GCP. This end-to-end prioritization of information and alerts streamlines the investigation process and greatly improves SOC efficiency. With the incorporation of cloud signals, the company has renamed Microsoft 365 Defender to Microsoft Defender XDR to better represent its capabilities that broadly span multiplatform and multicloud assets.
2021. Microsoft is buying cybersecurity startup RiskIQ
Microsoft has announced its acquisition of RiskIQ, a cybersecurity company based in San Francisco, for a reported $500 million. RiskIQ specializes in providing organizations with threat intelligence and cloud-based software-as-a-service solutions. The company extensively analyzes the web, gathering information about websites, networks, domain name records, certificates, and WHOIS registration data. By offering customers visibility into assets, devices, and services beyond their firewall, RiskIQ enables organizations to secure their assets and reduce their vulnerability to malicious actors. Notably, RiskIQ's data played a significant role in the discovery and understanding of Magecart, a collective term for groups that inject credit card-stealing malware into vulnerable websites.
2016. Cisco acquired cybersecurity-as-a-Service provider CloudLock
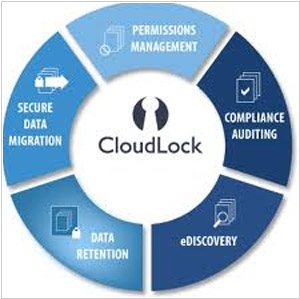
Cisco has revealed its intention to acquire CloudLock, a cloud-based security provider, for $293 million. CloudLock employs APIs to empower enterprises to apply and oversee security measures on shared and stored documents and other content within cloud-based applications. Its compatibility extends to popular applications like Office365, Google Drive, Salesforce, and numerous others. The primary focus of CloudLock lies in delivering robust security and enforcing policies to safeguard documents, regardless of the device used for accessing them. It also enables granular controls based on location, enhancing data protection capabilities.