Black Duck vs Veracode
November 09, 2023 | Author: Michael Stromann
Black Duck and Veracode are both significant players in the application security space, but they focus on different aspects of the development lifecycle, with Black Duck specializing in open-source security and Veracode providing a broader application security testing solution.
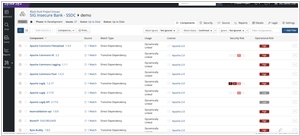
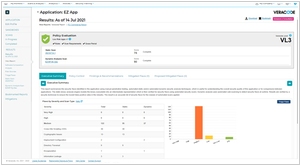
One key difference is the primary focus of each tool. Black Duck, now part of Synopsys, is renowned for its expertise in open-source security. It analyzes an application's dependencies and components to identify vulnerabilities and license compliance issues within open-source libraries and third-party code. This is particularly crucial in today's software development landscape, where the use of open-source components is prevalent. On the other hand, Veracode offers a comprehensive application security platform that includes both static application security testing (SAST) and dynamic application security testing (DAST), covering a broader range of security issues within the application code and its runtime environment.
Integration into the development workflow is another area where these tools differ. Black Duck is often integrated into the build and deployment processes, providing developers with insights into the security and compliance of their open-source components early in the development lifecycle. This allows teams to address issues before they become critical. Veracode, while also supporting integrations into the development pipeline, has a more comprehensive approach that extends to runtime analysis, ensuring a thorough security assessment across various stages of the development lifecycle.
See also: Top 10 Application Security Software
One key difference is the primary focus of each tool. Black Duck, now part of Synopsys, is renowned for its expertise in open-source security. It analyzes an application's dependencies and components to identify vulnerabilities and license compliance issues within open-source libraries and third-party code. This is particularly crucial in today's software development landscape, where the use of open-source components is prevalent. On the other hand, Veracode offers a comprehensive application security platform that includes both static application security testing (SAST) and dynamic application security testing (DAST), covering a broader range of security issues within the application code and its runtime environment.
Integration into the development workflow is another area where these tools differ. Black Duck is often integrated into the build and deployment processes, providing developers with insights into the security and compliance of their open-source components early in the development lifecycle. This allows teams to address issues before they become critical. Veracode, while also supporting integrations into the development pipeline, has a more comprehensive approach that extends to runtime analysis, ensuring a thorough security assessment across various stages of the development lifecycle.
See also: Top 10 Application Security Software